How secure is our digital world?
In today’s digital landscape, technology is used every day by many people around the world. We surf the web, send emails, and communicate with co-workers without thinking about whether this communication is secure.
The security of our digital communication originates from the 1980s when the current methods of encryption were invented. Algorithms such as Rivest-Shamir-Adleman (RSA), Diffie-Hellman (DH), and Elliptic Curve Cryptography (ECC) are all based on mathematical problems that cannot be easily solved by classical computers that function on binary bits [1][2][3]. To break each of these algorithms, classical computers would take countless years, and therefore our current communication channels are deemed safe.
However, a new player has entered our world and is radically changing the way we have to protect our digital selves. This player is called quantum computing and is, in some ways, a double-edged sword.

Quantum computing: A double edged sword
Quantum computing, also first conceptualized in the 1980s, has made significant progress in recent years. While today’s quantum computers cannot yet break traditional encryption, the potential is real and growing. Peter Shor’s 1994 algorithm demonstrated that quantum computers could eventually decrypt widely-used encryption methods like RSA, DH, and ECC. Though we’re not there yet, important bodies in the world, such as the G7, have recognized the threat on the horizon [4].
However, threats are not the only thing that quantum computers will bring. There are many opportunities that come with this new technology, such as quantum simulation for predicting new chemical reactions, quantum sensing to gain new insights from systems or infrastructures, and many other implications [5].
The fight against Shor
As quantum computing advances, the need for quantum-safe encryption grows. To fight the risk that Shor’s algorithm raises, the National Institute of Standards and Technology (NIST) has been working on selecting post-quantum cryptography (PQC) standards [6]. These new encryption standards were released in August 2024 and are designed on a different family of mathematical problems that will be very hard to solve for both classical and quantum computers. They can withstand live quantum attacks, offering protection for critical infrastructures like banking, military operations, and energy grids.
Although the protection against live quantum attacks seems sufficient, another threat is lurking called Harvest-Now Decrypt-Later (HNDL). This scheme stores long-term confidential information now and decrypts it later when a large operating quantum computer is available, making the urgency to migrate even higher. A general overview can be made of these threats, how the industry should react, and what the development of standards is [9].
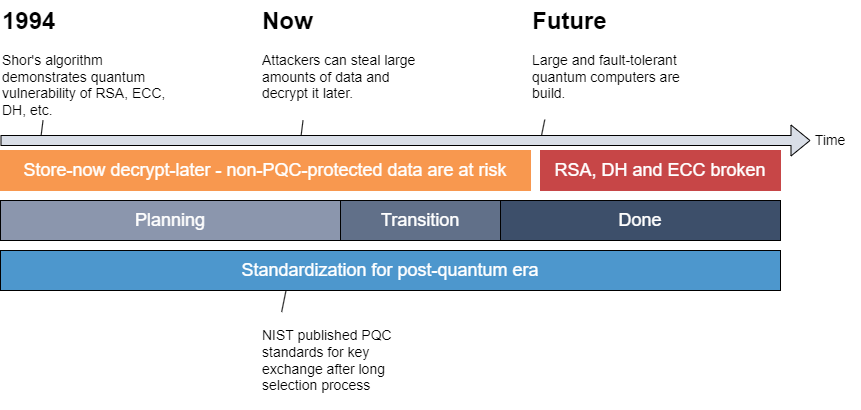
As can be seen in Figure 1, if the critical infrastructures want to protect their private data and ensure energy security for the country in the future, they must be planning for the transition at this point.
Standards as foundation
Standards are very important when looking at the migration towards a new technology. They help legitimize technological developments and offer a platform for joint innovation development [7]. Now that the basis has been established by NIST, the implementation and planning of the road towards the new PQC standard will be very challenging. Low awareness, reliance on third-party vendors, and the complexity of implementing these standards make the transition challenging [8]. This raises the question: How can industries, especially critical ones like energy, navigate this intricate process?
One thing is clear: Firms must work together, collaborate, and strive for an open way of working. Only then does this technology stand a chance to be implemented before it is too late [8].

The Dutch energy sector
The Dutch energy sector is an example of a vulnerable infrastructure. It consist of a government-owned transmission system operator (TSO) called TenneT, and works together with distribution system operators (DSOs) like Stedin and Alliander. Every day, the DSOs and big consumers communicate their expected energy use to the Balancing Responsible Party (BRP). Based on those numbers, the BRP tries to balance the daily consumption and production of energy. Therefore, it can be deducted that having secure communication between the parties is vital.
To determine what part of Dutch energy network is most critical, we must look at the energy hierarchy. High voltage lines are at the top of the hierarchy, but there are fewer of them. In contrast, low voltage lines are at the bottom of the hierarchy, but there are many more of them. All mid and low voltage lines are powered by the high voltage lines, making the high voltage lines the most critical in terms of energy security.
Besides the criticality, two other characteristics can be derived: number of stakeholders and bargaining power. The number of stakeholders in the high voltage network is low cause it is managed by only 1 party. The number of stakeholders in the middle and low voltage network is higher because they are managed by DSO’s. At last, the bargaining power of the network sectors is compared with each other. The middle and low voltage networks pay the high voltage network to use their grid. Therefore, the bargaining power of the high voltage player is higher.
These three characteristics are displayed in Figure 2, and all given a value.
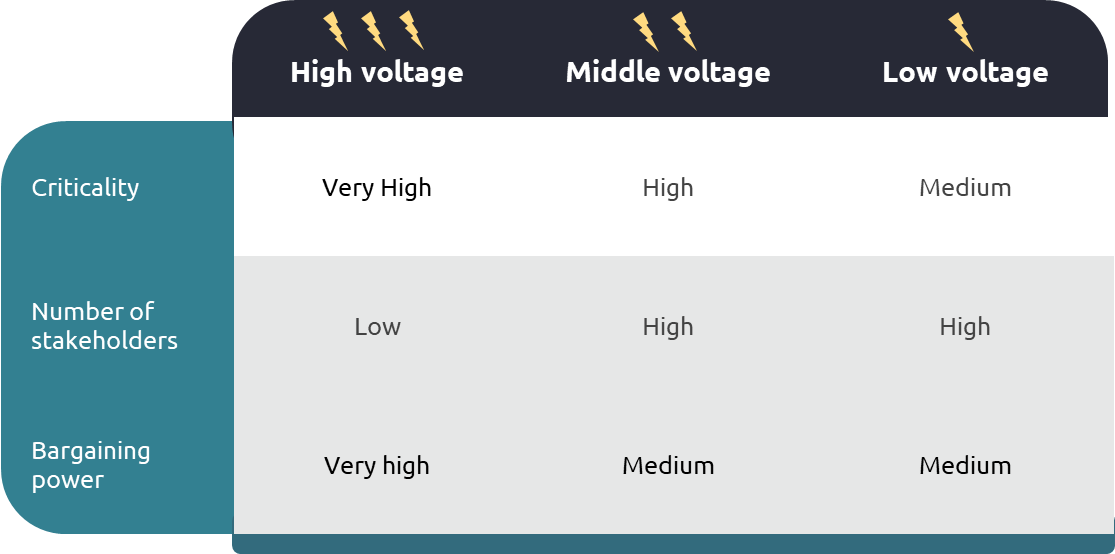
When combining the values that are presented in Figure 2, it can be deduced that the first starting point in the transition towards PQC in the Dutch energy network are the high voltage stakeholders.
Together with the encryption threats that have been presented in Figure 1 the following problem statement can be derived:
The adoption rate of post-quantum cryptography in the high voltage energy network sector is too slow relative to the potential decryption threats posed by quantum computers.
Next steps
In order to understand how to get a point of full adoption, we must understand what organizational adoption entails and how to influence it. In the next blog, organizational adoption will be addressed.
References
[1] Rivest, R. L., Shamir, A., & Adleman, L. (1978). A method for obtaining digital signatures and public-key cryptosystems. Communications of the ACM, 21(2), 120–126. https://doi.org/10.1145/359340.359342
[2] Diffie, W., Diffie, W., & Hellman, M. E. (1976). New Directions in Cryptography. IEEE Transactions on Information Theory, 22(6), 644–654. https://doi.org/10.1109/TIT.1976.1055638
[3] Miller, V. S. (1986). Use of Elliptic Curves in Cryptography. Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics), 218 LNCS, 417–426. https://doi.org/10.1007/3-540-39799-X_31a
[4] G7 CEG. (2024). G7 CYBER EXPERT GROUP STATEMENT ON PLANNING FOR THE OPPORTUNITIES AND RISKS OF QUANTUM COMPUTING. https://home.treasury.gov/system/files/136/G7-CYBER-EXPERT-GROUP-STATEMENT-PLANNING-OPPORTUNITIES-RISKS-QUANTUM-COMPUTING.pdf
[5] Brooks, M. (2023). Quantum computers: what are they good for? Nature, 617(7962), S1–S3. https://doi.org/10.1038/D41586-023-01692-9
[6] NIST. (2024b, August). Post-Quantum Cryptography | CSRC. https://csrc.nist.gov/projects/post-quantum-cryptography
[7] Wiegmann, P. M., Eggers, F., de Vries, H. J., & Blind, K. (2022). Competing Standard-Setting Organizations: A Choice Experiment. Research Policy, 51(2), 104427. https://doi.org/10.1016/J.RESPOL.2021.104427
[8] Capgemini. (2024, October 4). Transitioning to Quantum-Safe – Future-proofing Financial Services [Broadcast].
[9] Joseph, D., Misoczki, R., Manzano, M., Tricot, J., Pinuaga, F. D., Lacombe, O., Leichenauer, S., Hidary, J., Venables, P., & Hansen, R. (2022). Transitioning organizations to post-quantum cryptography. Nature 2022 605:7909, 605(7909), 237–243. https://doi.org/10.1038/s41586-022-04623-2



